 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Akamai Technologies Inc. researcher Ben Barnea has found two vulnerabilities in Windows Outlook clients that could cause remote code execution by attackers sending specially crafted sound file attachments.
Both build on previous exploits that have been previously discovered and only partially remediated by Microsoft Corp. in March, August and October. Barnea posted two blog posts (part one and part two) today that describe the exploits in detail in terms of how they work and how they can be prevented.
Outlook plays sound files, such as .WAV files, as a convenience, but now this is yet another way for malware to be deposited on a victim’s computer. The files are processed as shown in the diagram below through Windows’ Audio Compression Manager, because typically sound files employ some form of compression to keep file sizes more manageable. It is this component of Windows that’s ripe for one of the exploits.
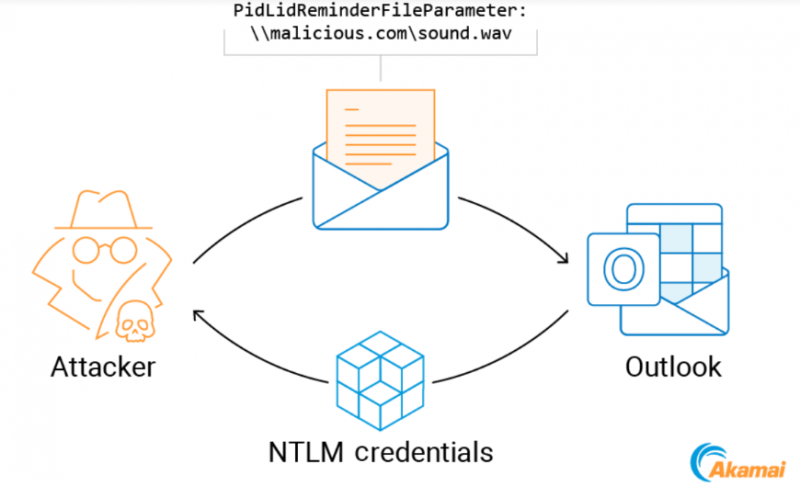
Barnea claims that Windows machines with the October 2023 software update installed are protected from these vulnerabilities. Additionally, Outlook clients that use Exchange servers patched with March 2023 software update, catalogued as CVE-2023-23397, are protected against the abused feature.
The March Outlook vulnerability was previously exploited earlier this month by a Russian state-sponsored malware group called Forest Blizzard, also known as Strontium. The group has been responsible for a variety of attacks, including one targeting Ukraine last year.
Barnea found a way to control a Windows machine when a user is emailed a reminder with an attached custom notification sound. The user doesn’t have to click on the attachment, so this is another so-called “zero-click” exploit.
Both of these exploits rely on very specific programming to take control over a victim’s computer, by combining the previous vulnerabilities in a specific order. Microsoft posted mitigation guidance back in March with suggestions on how to avoid the exploit.
Barnea says in his post that these are useful but don’t go far enough. He recommends “organizations use micro network segmentation to block outgoing SMB connections to remote public IP addresses and that you either disable NTLM in your environment or add users to the Protected Users group in Active Directory.”
THANK YOU